Syslog Viewer and Parser with Interactive Web UI
What is Syslog and Why You Need a Syslog Viewer
Syslog is a standard protocol used for system logging on Unix and Linux systems. It provides a centralized way to collect and store log messages from various system components, applications, and network devices. However, raw syslog entries can be difficult to read and analyze due to their dense format and high volume.
A dedicated syslog viewer like Logdy helps you:
- Parse complex syslog entries into structured data
- Filter logs by severity, facility, host, or process
- Search through large volumes of logs efficiently
- Visualize log patterns and identify issues quickly
- Monitor system events in real-time
Run Logdy with Syslog Logs
Logdy installation
Naviagate to docs for instructions on how to install Logdy. You can download a precompiled library, install using script or homebrew, lastly you can compile Logdy yourself.
On most Unix/Linux systems, syslog messages are typically stored in /var/log/syslog or /var/log/messages, though the exact location may vary depending on your system configuration.
To start viewing your syslog entries with Logdy (assuming it's added to PATH):
$ tail -f /var/log/syslog | logdyFor remote syslog servers, you can use SSH to stream logs:
$ ssh user@syslog-server "tail -f /var/log/syslog" | logdyEnter Logdy web UI
Visit the address provided in the console output after starting Logdy, by default it should be http://localhost:8080
Understanding Syslog Format
Let's examine a typical syslog entry:
<34>Oct 11 22:14:15 myhostname su[23747]: pam_unix(su:session): session opened for user root by (uid=1000)This syslog entry contains several components:
- Priority value (
<34>) - encodes both facility and severity - Timestamp (
Oct 11 22:14:15) - Hostname (
myhostname) - Process name and PID (
su[23747]) - Message content (
pam_unix(su:session): session opened for user root by (uid=1000))
Building a Syslog Parser with Logdy
Logdy allows you to parse syslog entries into structured data using a custom parser. The following TypeScript code implements a comprehensive syslog parser that extracts all relevant fields:
(line: Message): Message | void => {
const regex = new RegExp(
[
/(<\d+>)?/, // 1 - optional priority
/([a-z]{3})\s+/, // 2 - month
/(\d{1,2})\s+/, // 3 - date
/(\d{2}):/, // 4 - hours
/(\d{2}):/, // 5 - minutes
/(\d{2})/, // 6 - seconds
/(\s+[\w.-]+)?\s+/, // 7 - host
/([\w\-().\d/]+)/, // 8 - process
/(?:\[([a-z\d-.]+)])?:/, // 9 - optional pid
/(.+)/, // 10 - message
]
.map(regex => regex.source)
.join(''),
'i'
);
const facilities = [
'kern', 'user', 'mail', 'daemon', 'auth', 'syslog', 'lpr', 'news',
'uucp', 'cron', 'authpriv', 'ftp', 'ntp', 'logaudit', 'logalert', 'clock',
'local0', 'local1', 'local2', 'local3', 'local4', 'local5', 'local6', 'local7'
];
const severities = [
'emerg', 'alert', 'crit', 'err', 'warning', 'notice', 'info', 'debug'
];
const months = [
'Jan', 'Feb', 'Mar', 'Apr', 'May', 'Jun',
'Jul', 'Aug', 'Sep', 'Oct', 'Nov', 'Dec'
];
const parts = regex.exec(line.content.trim());
if (!parts) {
return line;
}
const priority = Number((parts[1] ?? '').replace(/\D/g, ''));
// Calculate facility and severity from priority
const facilityCode = priority >> 3;
const facility = facilities[facilityCode] || 'unknown';
const severityCode = priority & 7;
const severity = severities[severityCode] || 'unknown';
// Parse timestamp
const month = months.indexOf(parts[2] || '');
const date = Number(parts[3] || 0);
const hours = Number(parts[4] || 0);
const minutes = Number(parts[5] || 0);
const seconds = Number(parts[6] || 0);
const host = (parts[7] ?? '').trim();
const processName = parts[8] || '';
const pid = parts[9] ? Number(parts[9]) : undefined;
const message = (parts[10] ?? '').trim();
line.is_json = true;
line.json_content = {
priority,
facilityCode,
facility,
severityCode,
severity,
timestamp: `${parts[2]} ${parts[3]} ${parts[4]}:${parts[5]}:${parts[6]}`,
host,
process: processName,
pid,
message
};
return line;
}This parser extracts all the important information from syslog entries, including:
- Severity level (emergency, alert, critical, error, etc.)
- Facility (kernel, user, mail, system daemons, etc.)
- Timestamp information
- Host and process details
- The actual log message
Display columns and filters
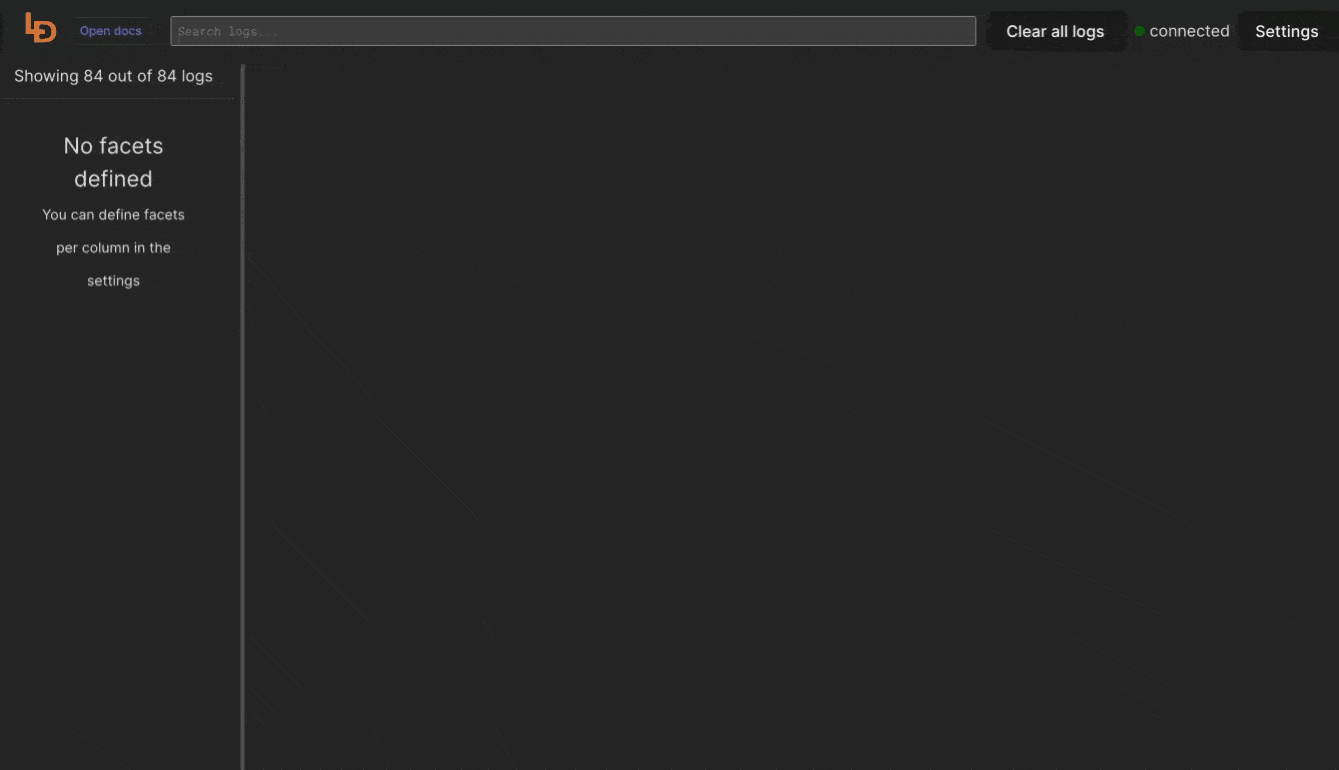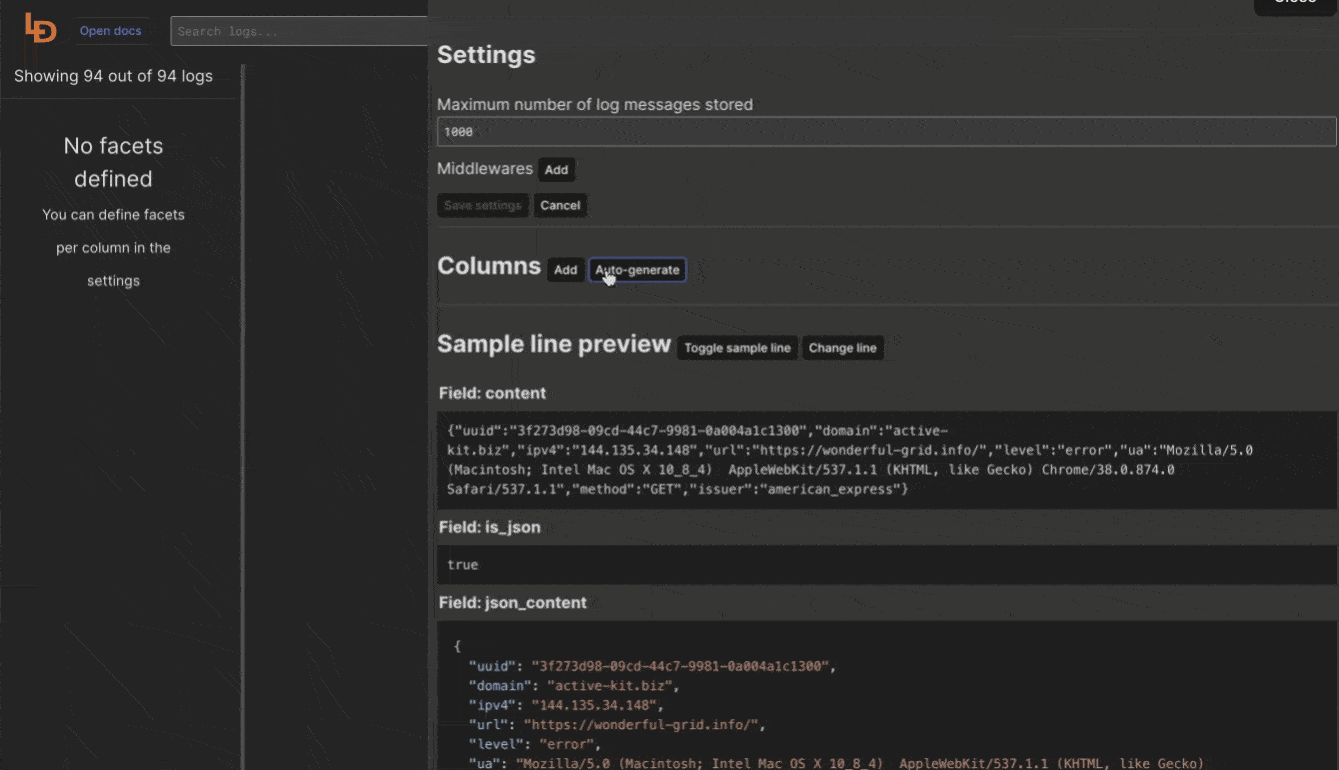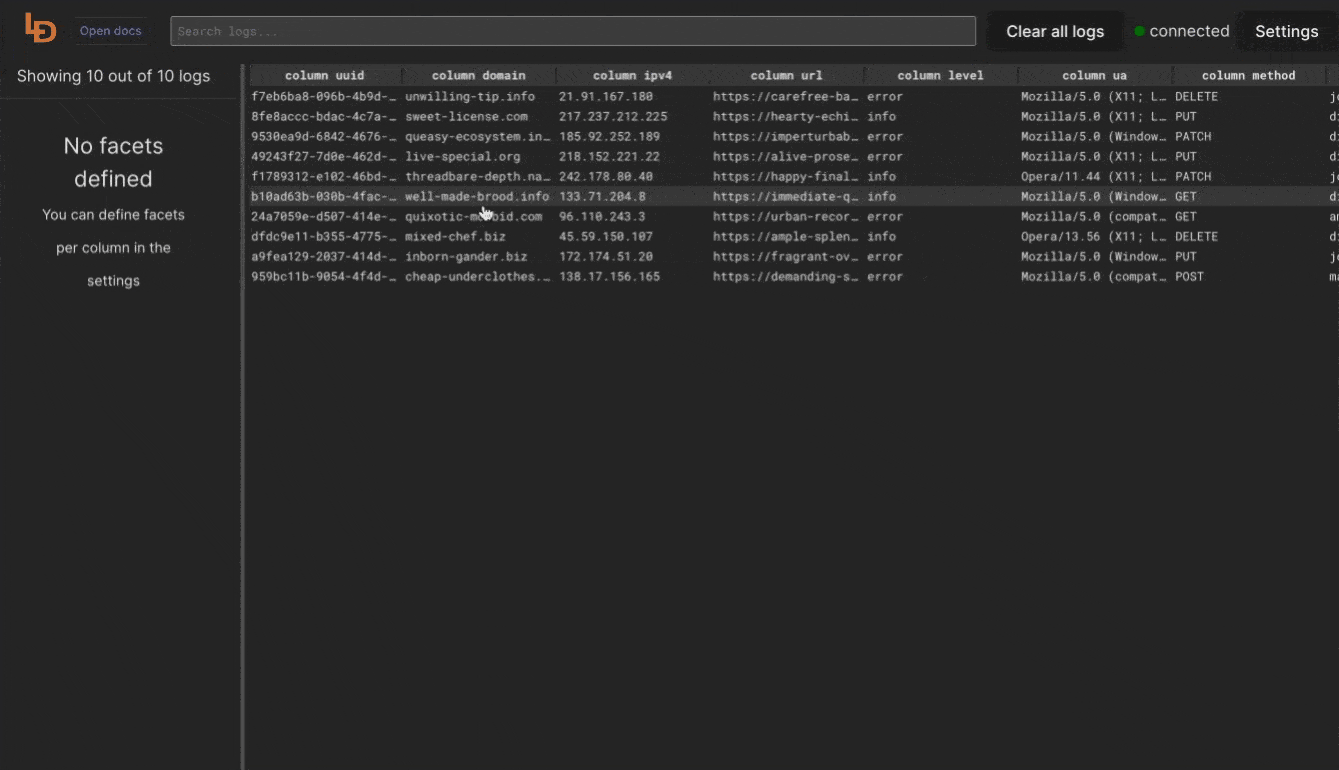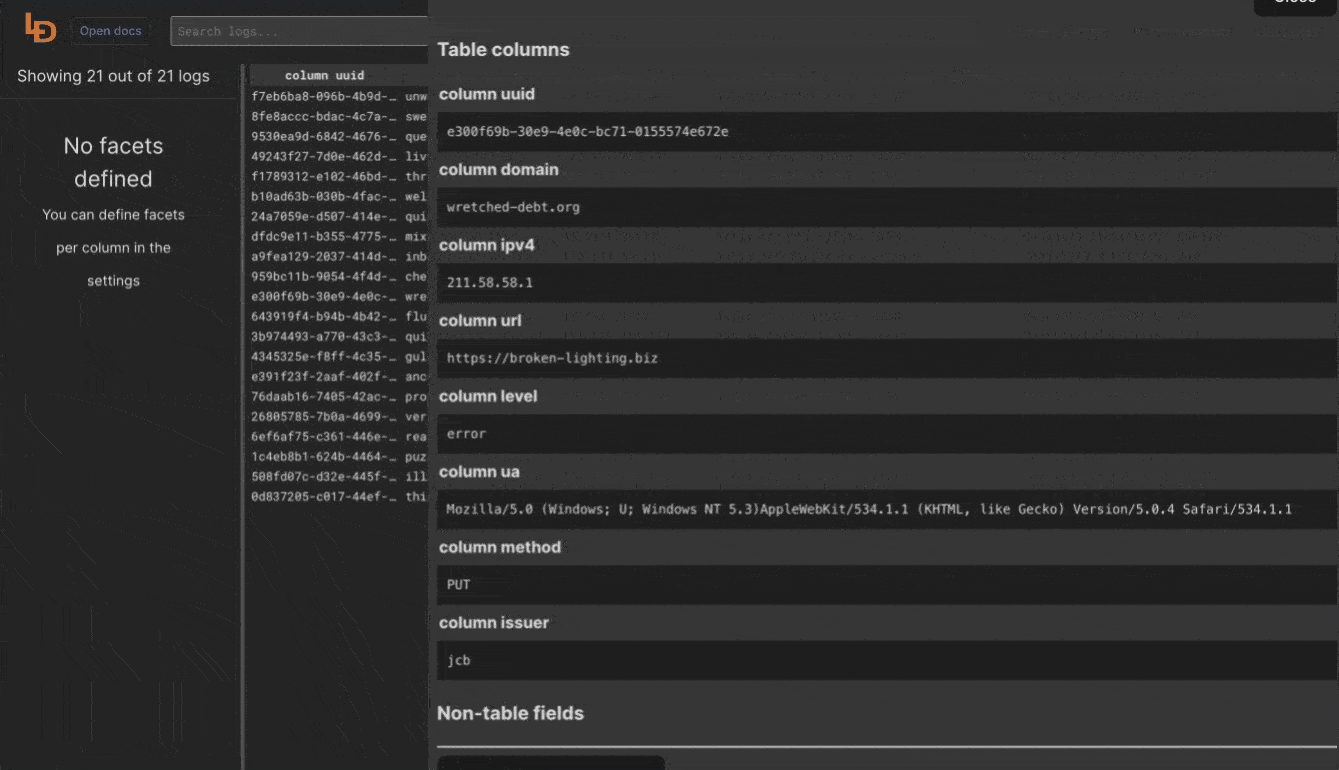
Logdy makes parsing and column selection a breeze. Use a built in "autogenerate" feature to generate columns based on JSON object present. Then you can make any adjustments and customizations. Based on the columns you can also emit facets or use another great feature to generate those automatically.
With a JSON object in place, you can use Auto-generated columns together with Faceted columns.
Customizing Your Syslog Viewer
Once your syslog entries are parsed into structured data, you can customize your Logdy interface to make the most of this information:
Color-coding by Severity
Set up row styling based on severity levels to quickly identify critical issues:
- Red for emergency and alert messages
- Orange for critical and error messages
- Yellow for warnings
- Default colors for informational messages
Useful Filters for Syslog Analysis
Create filters to focus on specific aspects of your logs:
- Filter by severity to focus on critical issues:
severity = "emerg" OR severity = "alert" OR severity = "crit" - Filter by facility to monitor specific system components:
facility = "auth" OR facility = "kern" - Filter by host to focus on specific servers in your infrastructure
- Filter by process to troubleshoot specific applications
Understanding Syslog Facilities and Severities
Syslog Facilities
Syslog facilities categorize the source of log messages:
| Facility Code | Facility Name | Description |
|---|---|---|
| 0 | kern | Kernel messages |
| 1 | user | User-level messages |
| 2 | Mail system | |
| 3 | daemon | System daemons |
| 4 | auth | Security/authorization messages |
| 5 | syslog | Messages generated by syslogd |
| 6 | lpr | Line printer subsystem |
| 7 | news | Network news subsystem |
| 8 | uucp | UUCP subsystem |
| 9 | cron | Clock daemon |
| 10 | authpriv | Security/authorization messages |
| 11 | ftp | FTP daemon |
| 12 | ntp | NTP subsystem |
| 13 | logaudit | Log audit |
| 14 | logalert | Log alert |
| 15 | clock | Clock daemon |
| 16-23 | local0-local7 | Locally used facilities |
Syslog Severities
Syslog severities indicate the importance of log messages:
| Severity Code | Severity Name | Description |
|---|---|---|
| 0 | emerg | System is unusable |
| 1 | alert | Action must be taken immediately |
| 2 | crit | Critical conditions |
| 3 | err | Error conditions |
| 4 | warning | Warning conditions |
| 5 | notice | Normal but significant condition |
| 6 | info | Informational messages |
| 7 | debug | Debug-level messages |
Conclusion
With Logdy's powerful parsing capabilities, you can transform raw syslog data into a structured, searchable, and visually intuitive format. This makes system monitoring and troubleshooting significantly more efficient, allowing you to quickly identify and resolve issues before they impact your users or services.
Whether you're a system administrator monitoring server health, a security analyst investigating potential threats, or a developer debugging application issues, Logdy's syslog viewer provides the tools you need to make sense of your system logs.
