What is an Application User Audit System?
Audit logs function as a centralized stream of user activity that security and compliance teams rely on to monitor information access, especially when investigating suspicious activities or during incident reviews. At first glance, they appear as simple entries containing events, timestamps, and payloads.
However, on a deeper level, they serve as comprehensive summaries that, when viewed collectively, create a detailed frame-by-frame narrative of system activities. This fine-grain audit trail provides organizations with complete visibility into who accessed what information, when, and how—essential for both security and regulatory compliance.
TIP
LogdyPro is a fit for building an Audit system storage on top. Thanks to a great compression capabilities it provides storage size reduction (thus costs) while retaining query capabilities.
Read customer case about how an storage for Audit system was implemented with LogdyPro.
What is an Audit Log?
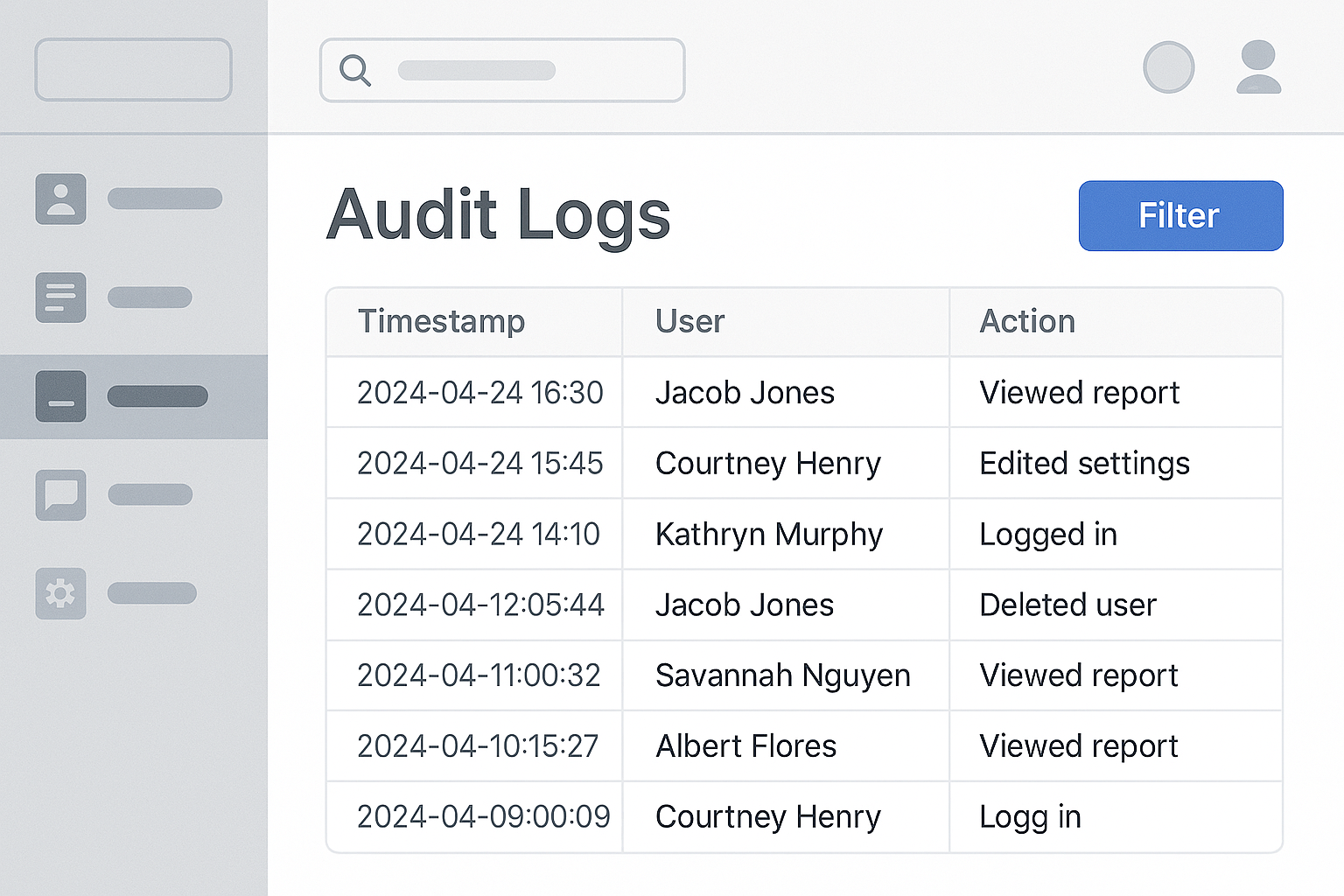
An audit log is a chronological record of system activities that documents specific events occurring within an application or system. Each log entry captures critical information about an action, including:
- The exact timestamp when the event occurred
- The specific action or event that took place
- The user or system component that initiated the action
- The affected resources or data
- The outcome of the action (success, failure, error codes)
When these individual records are compiled chronologically, they create a comprehensive audit trail that allows organizations to:
- Reconstruct activity timelines during security investigations
- Verify compliance with regulatory requirements like GDPR, HIPAA, or SOX
- Troubleshoot system issues by identifying when and where problems originated
- Monitor user behavior patterns to detect anomalies that might indicate security threats
- Provide evidence for legal proceedings or internal reviews
Effective audit logging is particularly crucial for applications handling sensitive data, where maintaining a verifiable record of all access and modifications is non-negotiable.
Why is an Audit System Important?
Implementing a robust audit system delivers several critical benefits for organizations:
Regulatory Compliance
Many industries face strict regulatory requirements that mandate detailed activity logging. Regulations like GDPR, HIPAA, SOX, and PCI-DSS explicitly require organizations to maintain comprehensive audit trails of data access and modifications. Failure to comply can result in severe penalties and legal consequences.
Security Incident Response
When security breaches occur, audit logs become invaluable forensic tools. They help security teams determine:
- The initial point of compromise
- What systems or data were accessed
- What actions were performed
- The timeline of the attack
- Potential data exfiltration
This information is crucial for containing breaches, assessing damage, and preventing future incidents.
Accountability and Non-repudiation
Audit logs create an immutable record of user actions, establishing clear accountability within organizations. This prevents situations where users can deny performing specific actions, as the audit trail provides definitive evidence of who did what and when.
What Audit Logs Store
Comprehensive audit logs capture multiple dimensions of system activity:
Action Details (What Happened?)
Audit logs document specific events such as:
- Resource creation, modification, or deletion
- Authentication attempts (successful and failed)
- Authorization decisions (access granted or denied)
- Configuration changes
- Data exports or downloads
- Administrative actions
Each event is categorized and described with sufficient detail to understand exactly what occurred.
User Information (Who Did It?)
Identifying the actor behind each action is crucial for accountability:
- User identifiers (username, user ID)
- Role or permission level
- Session identifiers
- Associated accounts (e.g., customer or organization ID)
This information establishes clear responsibility for every logged action.
Contextual Metadata
Additional context enhances the value of audit records:
- IP addresses (identifying the network origin)
- User agent strings (browser/device information)
- Geolocation data
- Request identifiers
- System states before and after the action
- Related business context (project IDs, customer references)
- Performance metrics
This metadata provides the surrounding context that transforms isolated log entries into meaningful narratives about system usage.
Drawbacks of Building User Audit Management in SaaS Applications
While audit logging is essential, implementing a robust audit system within a SaaS application presents several challenges:
Cost Implications
Audit logs generate substantial data volumes that grow continuously. Traditional database storage approaches can become prohibitively expensive as the application scales. For many SaaS providers, audit data storage costs can consume a significant portion of infrastructure budgets, directly impacting profitability margins.
Engineering Resource Allocation
Developing and maintaining a sophisticated audit system requires specialized engineering expertise. This diverts valuable development resources away from core product features and innovation. For startups and growing companies, this opportunity cost can significantly impact competitive positioning and time-to-market for new capabilities.
Operational Complexity
Audit systems must be highly reliable and performant, even under extreme load conditions. Ensuring that logging operations don't impact application performance requires careful architecture and ongoing optimization.
The "Insurance Policy" Paradox
Audit logging represents a classic "insurance policy" investment — when everything is functioning normally, its value may not be immediately apparent. However, during security incidents or compliance audits, its absence can be catastrophic. This creates a challenging prioritization dynamic, where critical infrastructure may be undervalued until it's urgently needed.
Enterprise Customer Requirements
Enterprise customers often have specific and stringent audit logging requirements that vary by industry and regulatory environment. Meeting these diverse needs while maintaining a cohesive product can create significant complexity and potential feature bloat.
These challenges highlight why many SaaS providers seek specialized solutions like LogdyPro that can handle audit logging requirements efficiently without diverting focus from their core business objectives.
What are the Requirements?
Our customer presented us with a clear challenge: could LogdyPro serve as the backbone of their audit log system, efficiently handling both high-volume data ingestion and complex querying requirements while maintaining compliance with their industry regulations?
This question represented more than just a technical integration—it was about finding a solution that would allow them to meet enterprise customer demands without compromising their business economics or engineering focus. The ideal solution needed to address both technical performance and business sustainability concerns.
TIP
LogdyPro is a fit for building an Audit system storage on top. Thanks to a great compression capabilities it provides storage size reduction (thus costs) while retaining query capabilities.
Read customer case about how an storage for Audit system was implemented with LogdyPro.
